Dalibor Kačmář: The media is being manipulated by adding fake data sources and passing them off as official news
They are not visible at first glance, but they have been growing multifold over the past two years - we are talking about cyber and hybrid threats, which are hitting the Czech Republic even more intensively than a year ago. In connection with cyber security, Microsoft annually publishes the so-called Digital Defense Report. When we discussed this document with Dalibor Kačmář, National Technology Officer at Microsoft Czech Republic, in our next episode of the CZ DIALOGUES discussion programme, he showed us documents for 2022 and 2023 for comparison. The latter document was one such document in terms of its volume, and this is roughly how we can measure the increasing dangerousness of these threats at a glance. The Czech Republic is likely to adopt a new law on cyber security this year, which both implements the European NIS2 directive and brings additional obligations to Czech critical infrastructure entities so that the impact of daily intense cyber attacks on our country is as low as possible.
Video: Interview with Dalibor Kačmář, National Technology Officer at Microsoft Czech Republic / CZ DEFENCE
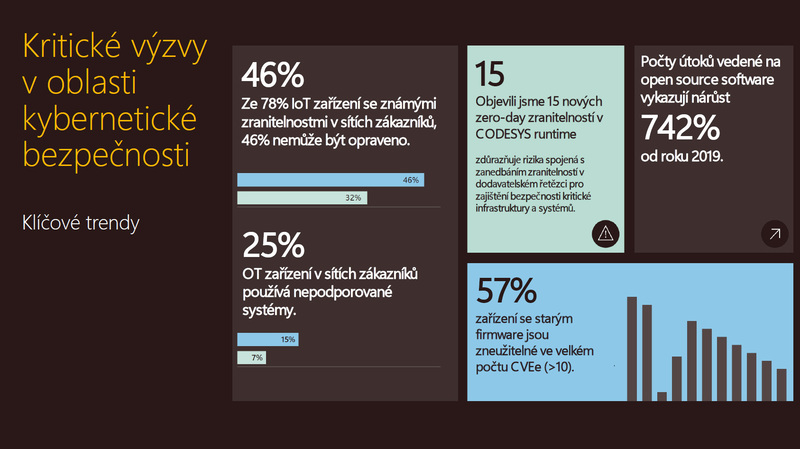
As we have already mentioned in the introduction, the scope and intensity of cyber and hybrid threats is constantly growing, which is also confirmed by the National Technology Officer at Microsoft Czech Republic. And the second relatively large area is dedicated to industrial devices and IoT (Internet of Things) systems, which today are proving to be just as dangerous and have a much greater impact if they are attacked," Dalibor Kačmář says in the interview, adding that attention to this area has increased significantly among state institutions and companies in recent years. "We can see this from the number of attacks that have at least been published in the media. As I said, state institutions or commercial companies are not excluded from these attacks, and therefore the attention is greater there. On the other hand, it shows that as the attack scene gets smarter, more sophisticated, it becomes basically a business," Kachmar judges.
The new law on cybersecurity envisages an expansion of the affected entities from the current four hundred to six thousand. According to Dalibor Kačmář, this will mean much greater obligations for many entities. And it's not just about buying hardware and software, but especially about having enough experts available to companies. "It's not just about buying some software or hardware, but it's about processes in the organisation and, for example, about increasing the responsibility of managers, where today, for example, legal liability is also arising. And last but not least, it is also about continuous education of both the obliged persons and the end users. Without that, you are simply leaving one part of the whole system unprotected. So continuous education is terribly important, because as the threats evolve, it is necessary to respond to them not only with software, hardware, but also with knowledge," says the National Technology Officer at Microsoft Czech Republic.
We were interested in how this global company, such as Microsoft, cooperates not only with armies around the world, but especially with our Army of the Czech Republic. According to Kačmar, Microsoft has been cooperating with the Czech Army for many years. "We are a supplier of a number of systems, but I would say that it is not just about a supplier-customer relationship, but it is currently mainly about building innovation. The Army, like every other sector, needs to innovate and I am glad that today the Army of the Czech Republic has the means and energy for innovation," says Dalibor Kačmář. In particular, it is about technologies using artificial intelligence, which can be used in many situations that the army needs. "On the other hand, if we stay on the topic of cyber security, the army also has its parts that are dedicated to cyber protection or defence. And this is where we cooperate with these organisations to transfer information that can serve them for better defence, to build a better cyber security defence," adds the National Technology Officer at Microsoft Czech Republic. Microsoft is thus contributing to the modernisation of the Czech Armed Forces with software technologies whose importance in the equipment and armament of the army is steadily growing. This includes, for example, the detection of cyber attacks, disinformation campaigns, manipulation campaigns, etc.
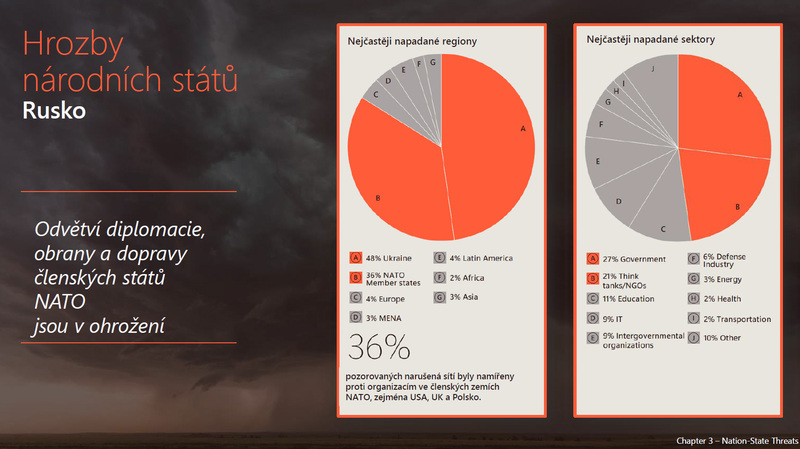
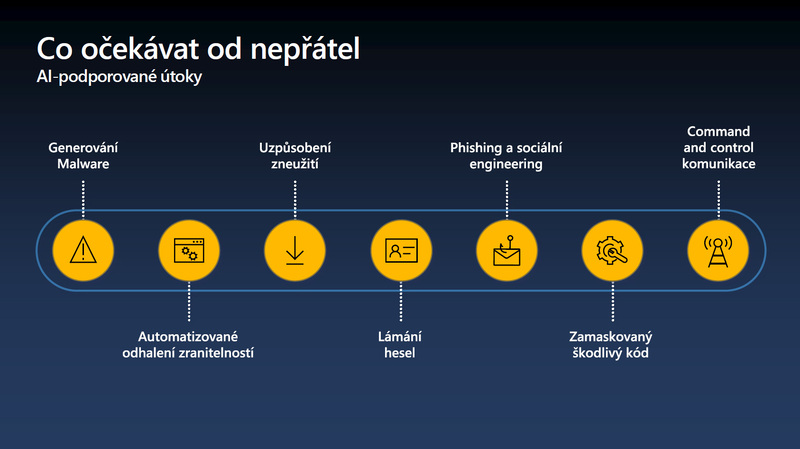
Weapons and armaments used in warfare today are no longer just guns, tanks, machine guns, missiles, but also sophisticated systems controlling cyberspace. It is therefore a good idea to focus, among other things, on who the attacker is. According to Dalibor Kačmář, the attackers, who today are economically motivated and highly professionalised, need to be named. "I would say that there is almost an industrialization of the industry going on here. The goal is, of course, to make a profit. On the other hand, if we get to the level of state protection, protection of soft targets, etc., then of course there are groups that are supported by nation states attacking. In our case, and this is also part of the latest edition of the Microsoft Digital Defence Report, there are examples of how attacks are taking place from the territory of the biggest enemies, which today are Russia, China and Iran. When we look at, for example, attacks from Russia or by Russian-backed groups, they are, of course, directed primarily at entities in the conflict zone, i.e. in Ukraine, but secondarily at entities that are part of NATO and that directly or indirectly support the Ukrainian side. The Czech Republic is a strong player here, and therefore we are, or potentially will be in the future, the target of such attacks," says the National Technology Officer at Microsoft Czech Republic.
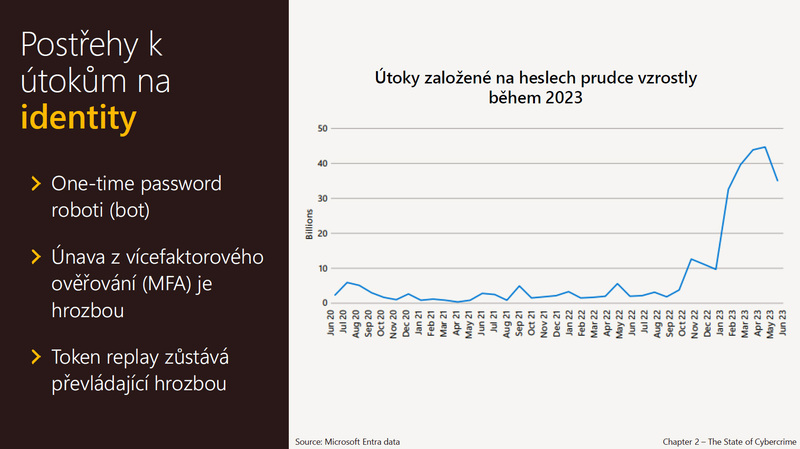
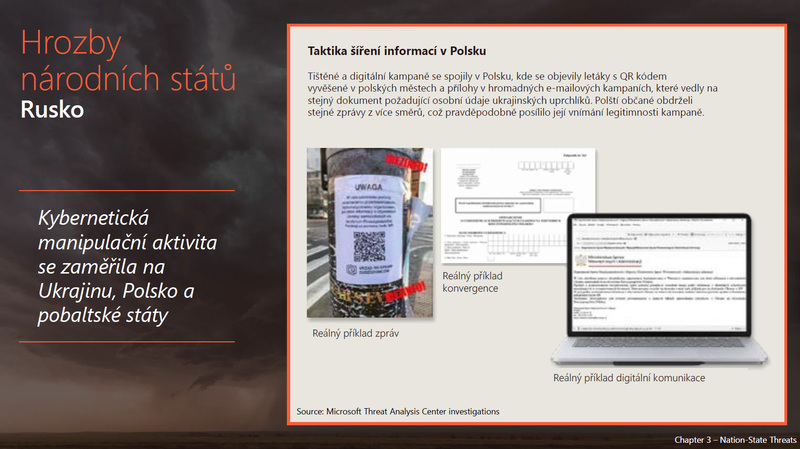
It is good to note that the methods and level of cyber attacks have changed. "Many people cannot imagine the concrete impact of these attacks on the running of the country. They can't imagine what happens to stolen data, for example. If we come out of the experience of the war in Ukraine, it is a demonstration of hybrid warfare, where cyber attacks were initially combined in a time-coordinated manner with ground attacks. Nowadays, the third part, i.e. disinformation or manipulation campaigns, is added much more, when the war goes into a long-term fatigue state," says Dalibor Kačmář. "This is what the attackers use to manipulate the opinion of the population, which is tired of war. And of course they abuse the information that is in the media. They use manipulation of the content. There is a specific manipulation of, for example, the media, that is, adding false sources of data and passing them off as official news and so on, or using prominent figures to make some statements that they have not made. In this way, they try to moralise or convert public opinion to the other side and thus weaken the defence," says Dalibor Kačmář.

And the published Digital Defense Report, as well as other documents, show what these manipulation campaigns look like. "Let's stay with Russia for a moment. The targets that are being attacked are changing. At the beginning of the conflict, of course, critical infrastructure was targeted, the energy system or the communications system. In the last six months there have been major attacks on industry and agriculture. And it started with Russia's withdrawal from the grain agreement and the subsequent attacks on organisations that were trading or transporting grain, thereby undermining agricultural production and stopping the flow of Ukrainian grain, for example, to countries in need, affecting, we estimate, on the order of a million people.

Which is significant, especially when we look at the primary buyers of Ukrainian grain. So, of course, you affect the recipients themselves, but you also affect the producers, because the producers cannot continue to produce because, for example, their warehouses are full, etc. So this is also part of the war today, and it is related not only to the attacking, cyber attacking of IT systems, but also, for example, to the disinformation operations that are associated with it," says Dalibor Kačmář, National Technology Officer at Microsoft Czech Republic, in the CZ DIALOGUES programme.
In the interview, we also discuss, for example, how our personal data that we use to log in on the Internet is at risk or how big a threat we are to cyberspace and protection against attacks. To learn more, listen to the full interview at the top of this article.



















