Dalibor Kačmář: Cyber attack precedes conventional attack
While contemporary armed conflicts are still being fought in a conventional manner using conventional weapons, in addition to this classic physical battlefield, more and more attention is shifting to a new type of battlefield, which is cyberspace. Sophisticated cyber-attacks target not only critical infrastructure, but far more often state institutions, companies and specific individuals, where such threats can effectively damage an adversary without the use of a single bullet. In the next episode of our discussion show CZ DIALOGY, we talked to Dalibor Kačmář, Director of Technology Standards at Microsoft, about how the Czech Republic is protected from cyber attacks, what potential threats we face and how to build an effective defence in cyberspace.
Video: Interview with Dalibor Kačmář, Director of Technology Standards at Microsoft / CZ DEFENCE
There are a lot of attacks on the Czech Republic as a NATO member country in the geopolitical context. "There is enough room to improve many things. But I think the Czech Republic is relatively well protected. If only because we have a large number of organisations that deal with cyber defence, whether, say, in the state sector or ultimately in the military environment," says Dalibor Kačmář. We wondered who the enemy actually is – is it individuals, groups, organisations? "Cybercrime is evolving to a large extent. If we look back many years, it might have been individuals or some organised groups with their own goals, whether economic or political," says Kačmář. According to him, cybercrime today is actually an industry where it is not easy to untangle the connections. Special groups specialise in different parts of the cyber spectrum. "Today the work is divided into different parts. The groups are cooperating with each other. Each of them is good in his or her area and a basically legitimate - if you can call it that - business is created. For example, there are specialists or groups that are dedicated to attacking some infrastructure, for example, stealing identities. But they do not continue with the attack and then sell the stolen identities. Someone else knows why they need those identities and what they want to do with them, and they carry out some successful or less successful attack. But that may not be the end of the operation either," Kačmář explains.
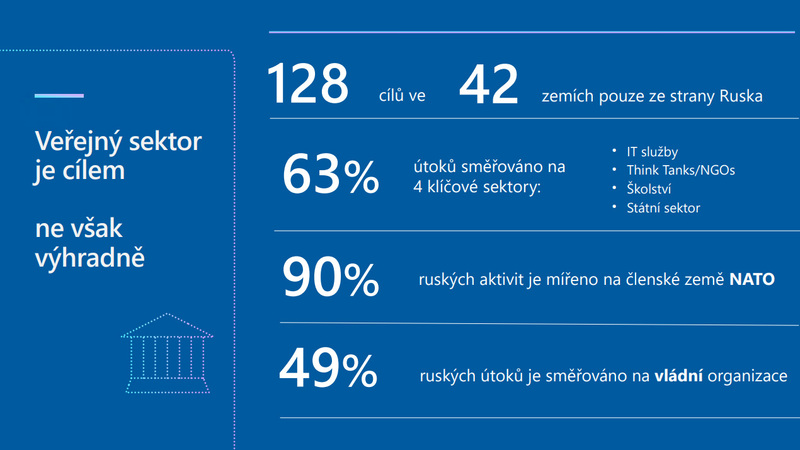 Picture: Cyberattack targets | Dalibor Kačmář / Microsoft
Picture: Cyberattack targets | Dalibor Kačmář / Microsoft
Part of defending against a potential cyber-attack is the very important compliance of employees with security rules. Any external access to a company or institution's system is a problem and a weak point. "What is happening in the cyber scene today is that attackers are not breaking in, they are logging in," says Kachmar, who adds: "If I liken it to house burglaries, they don't break down our front door, they steal the keys and enter the house in a perfectly legitimate way. It's far less detectable. If I have the keys and I'm the person who is privileged, then because of my privileges, the attacker has a much easier role to move around in the system. Why I say this is that most attacks today are done through identity theft. That said, if there's one area where I would like to do some more protection, it's in the area of securing identities." There are a number of tools that can identify an individual's behaviour, for example. "If somebody logs in one minute from the Czech Republic, the next minute from India, the next minute from Russia, etc., that is obviously suspicious. Such behaviour cannot be legitimate. Today, we have defensive systems that can not only technically protect against identity breaches, but also track and monitor an individual's behaviour. They check if the behaviour is different and indicates some attempt to break in or, heaven forbid, if there is already movement in the IT system, which is the next step after a successful penetration," explains Kačmář.
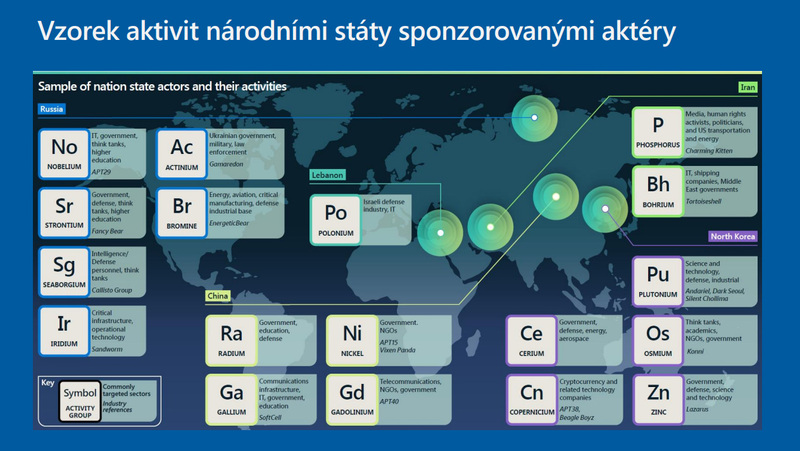 Picture: Sample of activities by nation-state sponsored actors | Dalibor Kačmář / Microsoft
Picture: Sample of activities by nation-state sponsored actors | Dalibor Kačmář / Microsoft
Hybrid warfare is now an integral part of conventional warfare, which is also evident in the Ukrainian conflict. "We already have clear clues that say that, for the most part, the cyber attack precedes the conventional one. Because if the attackers correctly attack the infrastructure in the area where they need to attack, they paralyse the corresponding organisations or authorities, which then have to act. And the conventional attack follows. Of course, the resulting effect on the attacked area is significantly greater," explains Dalibor Kačmář. As in other cases, the Ukrainian war is a lesson for software developers and an inspiration for further work. The key work is then finding attack vectors. After all, cyber operations take place through them, so it is important to know about them in order to prevent them. "According to one of the statistics that we have done recently we are able to defend against on the order of eighty percent of attacks, and that is just by sort of simple security hygiene. This is usually not in place," adds Dalibor Kačmář, director of technology standards at Microsoft.
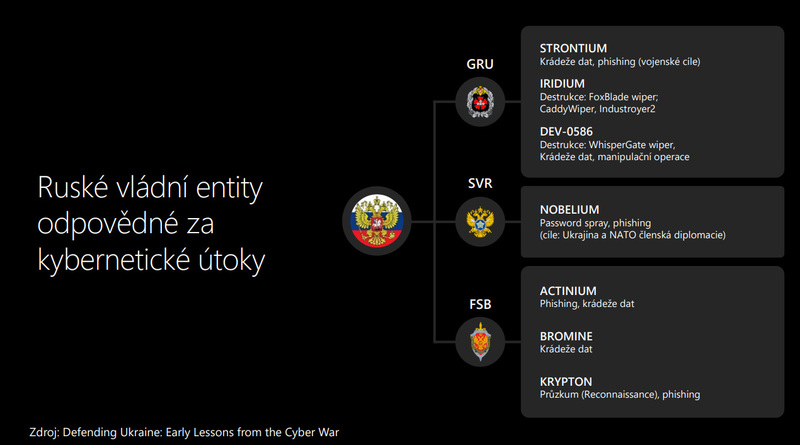 Picture: Russian government entities responsible for cyber attacks | Dalibor Kačmář / Microsoft
Picture: Russian government entities responsible for cyber attacks | Dalibor Kačmář / Microsoft
Artificial intelligence is playing an increasingly important role in cyberspace. "Artificial intelligence is used today in cyber defence mainly to detect user and system behaviour. In the moments when an attacker gets into a system and is really unobserved, it is important to detect that he is there based on his activities and, of course, to identify the places that are attacked," says Kačmář. This cannot be detected by some simple human analysis, this is where artificial intelligence must be used. "What is important is the ability to monitor the behavioural patterns of systems and people and identify threats that will occur or penetrations that have already occurred. The second area for the action of artificial intelligence are activities related to identifying some disinformation operations and finding the content or the originators that are responsible for or are the source of the disinformation operations," adds Dalibor Kačmář.
 Picture: In this episode of our discussion show CZ DIALOGY, we talked with Dalibor Kačmář, Director of Technology Standards at Microsoft | Michal Pivoňka / CZ DEFENCE
Picture: In this episode of our discussion show CZ DIALOGY, we talked with Dalibor Kačmář, Director of Technology Standards at Microsoft | Michal Pivoňka / CZ DEFENCE
Data storage also plays a role, with large amounts of this data residing in cloud storage. We wondered what role cloud storage can play in war conflicts such as the one in Ukraine. At the beginning of the war, Ukraine had its IT environment unreservedly located on its territory. "Of course, the moment there were such massive attacks targeting the infrastructure and critical infrastructure of the state, there was a high risk that the IT infrastructure would be damaged," Kachmar says, adding that at the beginning of the war, the damage was indeed significant. "Today, many operations are done through IT and it is therefore advisable to move the systems in your operation out of the territory.
 Picture: It is important to be able to monitor patterns of system and human behavior and identify threats that will occur or intrusions that have already occurred. | Shutterstock
Picture: It is important to be able to monitor patterns of system and human behavior and identify threats that will occur or intrusions that have already occurred. | Shutterstock
Microsoft, but also some other global companies have helped Ukraine to a very large extent to transfer this IT. And where else but to the cloud environment and continue to operate systems independently of what is physically happening in the territory during the conflict," explains Kachmar. He says a similar problem occurred in the case of the earthquake in Turkey. A number of countries that feel threatened have already moved to a cloud solution. Companies like Microsoft are now a huge target of cyber attacks by hackers. "On the other hand, we have thousands of people in our company who are specialised in cyber security and defence," concludes Kačmář.
 Picture: Top six contributors to vulnerabilities | Dalibor Kačmář / Microsoft
Picture: Top six contributors to vulnerabilities | Dalibor Kačmář / Microsoft
Dalibor Kačmář is also the author of the so-called ten rules of conduct in cyberspace, which describes ten areas that need to be addressed to keep IT secure. "Defending your identity, not letting your keys out of your pocket, stealing your ID, etc.

Picture: Dalibor Kačmář is also the author of the so-called ten rules of behavior in cyberspace | Dalibor Kačmář / Microsoft
Another thing that happens very often is the fact that the IT systems I run as an individual or as an organisation are not up to date. If I hesitate to update and don't have the patches installed, my system naturally becomes a honeycomb and attracts attackers to exploit this vulnerability," explains Kačmář. According to him, the world of IT defence is no longer just a firewall or antivirus, which was enough before. "We really need to approach IT in a way that anticipates an attack and minimises the damage that can occur in such an attack. We call this the zero trust principle," adds Dalibor Kačmář, director of technology standards at Microsoft.
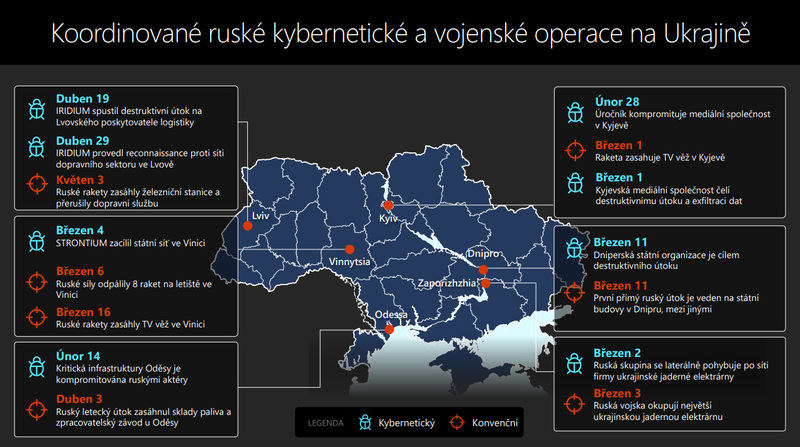 Picture: Cyber and military operations in Ukraine - the continuity is obvious | Dalibor Kačmář / Microsoft
Picture: Cyber and military operations in Ukraine - the continuity is obvious | Dalibor Kačmář / Microsoft
In our interview with Dalibor Kačmář, we also discussed the growth of cybercrime and the profits from it, and we were also interested in what such a ransomware attack looks like. We also discussed lessons learned from the cyber war in Ukraine, working with cloud storage, Russian espionage, and the global impact of Russian manipulation.
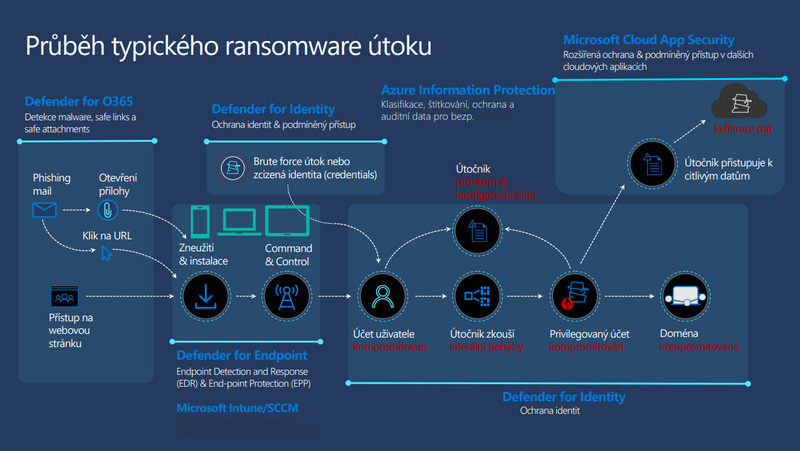 Picture: Progress of ransomware attack | Dalibor Kačmář / Microsoft
Picture: Progress of ransomware attack | Dalibor Kačmář / Microsoft
If you're interested in our full interview with Dalibor Kačmář, watch the video at the top of this article.



















